-
- About Taroko
- News
- Corporate Governance
- Investor
- Sustainability
- Recruitment
- Contact Us
- English WooCommerce not Found
- Newsletter
Home / Governance / Information Security Framework
The authority and responsibility unit of the company’s information security is the information department, which has an information supervisor and several professional information engineers, who are responsible for formulating the company’s information security policy, planning information security measures, and implementing relevant information security operations.
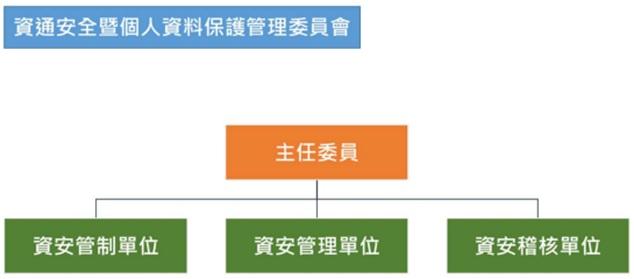
The audit office of the company is the audit unit of information security supervision, if the audit finds deficiencies, it immediately requires the inspected unit to propose relevant improvement plans and report them to the board of directors, and regularly tracks the improvement results to reduce internal information security risks.
Every year, the accountant conducts an information operation review, and if it is found to be deficient, it will ask for improvement measures and track the improvement results.
Based on the importance of information security, the responsible unit regularly reports to the board of directors on the governance and implementation of enterprise information security every year.
In order to strengthen the security management of information and ensure the confidentiality, integrity and availability of information, and to avoid intentional or unexpected threats from internal and external threats, the company’s information security facilities and management methods are divided into six major items as follows:
(1) Computer equipment security management
1. The company’s application servers and other equipment are set up in the special computer room, the access control of the computer room is used by sensor card access, and the entry and exit records are kept for check.
2. The computer room is equipped with independent air conditioning to maintain the operation of computer equipment in an appropriate temperature environment; And equipped with chemical fire extinguishers, which can be applied to general or electrical fires.
3. The main machine room is equipped with uninterruptible power and voltage stabilization equipment, and is connected to the company’s own generator power supply system to avoid Taipower’s accidental instantaneous power failure caused by the system crashing, or to ensure that the operation of the computer application system will not be interrupted in the event of a temporary power failure.
(2) Network security management
1. Strengthen network control, the entrance to connect with the external network, and configure enterprise-level firewalls to block illegal intrusion by hackers.
2. The connection operation between Taichung and Hsinchu computer room and Keelung office site to site uses data encryption to avoid illegal capture of data transmission process.
3. Colleagues who log in to the company’s intranet to access the ERP system remotely must apply for a VPN account, and can log in and use through the VPN security method, and all have usage records that can be audited.
(3) Virus protection and management
1. The server and the computer equipment of the colleague terminal are installed with protection software, and the virus pattern adopts automatic update method to ensure that the latest virus can be blocked, and at the same time, it can detect and prevent the installation of potentially threatening system execution files.
2. The antivirus system not only immediately isolates or deletes the viruses detected or intercepted, and actively issues infected and risky computer risk reports to facilitate management personnel to take corresponding actions.
(4) System access control.
1. The use of each application system by colleagues shall be accessed by the information unit through the system authority application procedure stipulated by the company and approved by the authority supervisor, and authorized by each system administrator according to the applied functional authority.
2. The password setting of the account stipulates the appropriate strength and number of words, and must be mixed with numbers and special symbols in order to pass.
3. When colleagues go through the procedures for leaving (suspending) from their posts, they must handle the information unit and delete the accounts of each system.
(5) Ensure the stable operation of the system.
1. System backup: build a backup system, adopt a regular backup mechanism, in addition to uploading a copy of the backup host in the computer room, the backup host 2 in the computer room and the backup host in the Hsinchu computer room are stored separately to ensure absolute security.
2. Disaster recovery drill: Each system implements a drill once a year, after selecting the reference point of the restore date, the backup media is stored back to the system host, and then the user unit confirms the correctness of the reply data in writing to ensure the correctness and validity of the backup media.
3. Lease two data lines of the telecommunications company, through bandwidth management equipment, the two lines are connected in parallel for backup use to ensure uninterrupted network communication.
(6) Information security advocacy and education and training
1. Regularly advocate. Require colleagues to change the system password regularly to maintain account security.
2. Lecture advocacy. Information security-related education and training courses are conducted for internal colleagues from time to time every year
3. Invest resources in information security management
(1) Network hardware equipment such as firewalls, email anti-virus, network management collection lines, etc.
(2) Software systems such as backup management software, VPN authentication, etc.
(3) Telecommunication services such as multiple lines, host backup services, intrusion prevention services, etc.
(4) Invest manpower such as: daily system status check, weekly regular backup and implementation of remote storage of backup media, at least twice a year information security advocacy education courses, annual system disaster recovery drills, annual internal audit of information circulation, accountant audit, etc.
(5) Information security manpower: set up information security supervisors and information security personnel, responsible for information security structure design, information security maintenance and monitoring, information security incident response and investigation, information security policy review and revision, and the information security supervisor reports to the board of directors at least once a year.
Spokesperson
General Counsel / Hsu Yung-Chang
Email: jerryhsu.trk@gmail.com
Acting Spokesperson
Equity Manager / Kelly Lo
Phone: 04-36118888#6661
Email: kelly.lo@trkmall.com.tw
Email: jessie.li@trkmall.com.tw

+886 4-3611-8888
+886 4-3611-6688
trk04690983@gmail.com

+886 4-3611-8888
+886 4-3611-6688
trk04690983@gmail.com